User Authentication and Authorization
This section describes how Genesys Intelligent Automation ensures that only authenticated and authorized users access Intelligent Automation environment specifically, and the Genesys software environment generally.
For more information about user authentication and authorization, refer to the User Authentication and User Authorization section of the Genesys Security Deployment Guide.
Internal and External Users
There are two types of users in Intelligent Automation:
- Internal users: Created and managed in Intelligent Automation. See the Users page in Intelligent Automation Help. These users are not subject to an external authentication engine; all authentication is done by Intelligent Automation. All authorization is implemented through Roles.
- External users: Created and managed in Genesys Configuration Server. Authentication is done internally by Configuration Server and sometimes by an external authentication engine, such as LDAP (Lightweight Directory Access Protocol), and RADIUS (Remote Authentication Dial In User Service). Authorization is done in Configuration Server. External users are supported starting in release 9.0.004.00.
The two user types mean that when creating a new user, the administrator must first decide whether to create the user in Intelligent Automation or in Configuration Server.
Prerequisites for external users
If you are working with external users, you must do the following:
- Enable Intelligent Automation to work with external users.
- Configure Intelligent Automation access to Configuration Server.
- Import a Solution Package Definition (SPD) file containing all role privileges, into the Genesys Configuration Database.
- Link tenant IDs in the Configuration Database to Intelligent Automation companies. Identify a default company for those users that might not belong to a tenant.
Configure working with external users
To configure Intelligent Automation to work with external users, set the parameter Login.ExternalAuthenticationMode to ConfigServer in the Default Server Settings tab under Administration in the Intelligent Automation interface:
The default value of this parameter is None, meaning that external users cannot log in to Intelligent Automation.
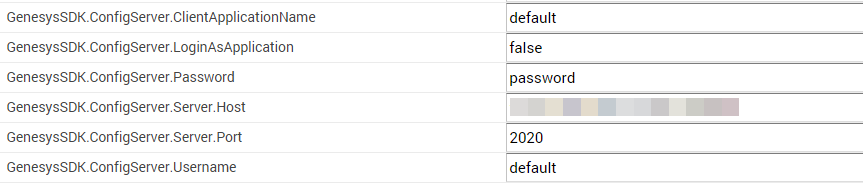
Configure access to Configuration Server
To configure Intelligent Automation to work with external users, Intelligent Automation must call upon Configuration Server to, among other things, validate the user. Therefore, you must provide the information required to access Configuration Server in the Default Server Settings tab, as follows:
Import SPD file into Configuration Database
A Solution Package Definition (SPD) file contains all role privileges for the associated solution. Without it, validated external users would be logged in with no permissions or roles. An SPD file called IA_SPD_Roles.xml is provided to you by Intelligent Automation if you choose to manage external users via Configuration Server. It must be imported into the Genesys Configuration Database. For information about installing the SPD file, see Solution Deployment or the Genesys Administrator Extension Developer's Guide.
Linking tenant IDs to Intelligent Automation companies
Each Intelligent Automation company should be linked to a tenant in the Configuration Database by specifying the DBID of that Tenant in the Configuration Server Tenant (DBID) field when configuring the company. When an external user logs into Intelligent Automation, the company corresponding to the user's Tenant is loaded for that user.
If a company is not linked to a particular tenant, or the tenant does not exist, you can specify a default company in the GenesysSDK.ConfigServerLogin.DefaultCompanyID parameter.
If a default company is not specified, any login by an external user without a linked tenant ID is rejected.
Two-factor Authentication
Two-factor authentication adds an extra layer of security by requiring users to verify their identity in two unique ways before being granted access to the application. When a user attempts to log in to the application with a username and password, an account protected by two-factor identification will also require the user to enter a dynamically-generated code delivered through a verified email address or phone number.
Intelligent Automation supports two types of two-factor authentication - internal authentication and external authentication.
Internal Authentication
With internal authentication, Intelligent Automation generates a code internally and delivers the code to the user's verified email address or phone number (SMS).
The process is as follows:
- If the user has more than one verified contact method, Intelligent Automation prompts the user to select an authentication method. For example, Press 1 to receive the code via email. Press 2 to receive the code via SMS. If the user has only one verified contact method, Intelligent Automation skips to Step 3 in this process.
- The user enters a response.
- Intelligent Automation generates the code and delivers it to the user's preferred contact method (SMS, for example).
- Intelligent Automation prompts the user to enter the code.
- When the user enters the code, Intelligent Automation checks the code and its timestamp.
- If the code and timestamp are valid, Intelligent Automation grants access. If the code or timestamp is invalid, Intelligent Automation prompts the user to enter another code, until the Maximum Attempts at Sending an Authentication Code value is reached.
External Authentication
With external authentication, Intelligent Automation hands the code generation and verification process over to an external authentication application, such as Google Authenticator.
The process is as follows:
- If the user has more than one verified contact method, Intelligent Automation prompts the user to select an authentication method. For example, Press 1 to receive the code via email. Press 2 to receive the code via Google Authenticator. If the user has only one verified contact method (in this example Google Authenticator), Intelligent Automation skips to Step 3 in this process.
- The user enters a response.
- The user retrieves the code from the external application and enters it into the Intelligent Automation application
- Intelligent Automation checks with the external application that the code is valid.
- The external application returns a the validation result (for example success).
- If the result is successful (i.e. the code is valid), Intelligent Automation grants access. If the result is unsuccessful (i.e. the code is invalid), Intelligent Automation prompts the user to enter another code, until the Maximum Attempts at Sending an Authentication Code value is reached.
Enabling Two-factor Authentication
Two-factor Authentication settings are enabled on the Applications > Two Factor Authentication Settings page in the Intelligent Automation user interface.
| Setting | Description |
|---|---|
| 'Contact Methods and Behavior | |
| Variable Name for Customer Email Address | The user's verified email address. |
| Variable Name for Customer Phone Number | The user's verified phone number. |
| Behaviour if No Verified Contact Method Available | Options?? |
| Maximum Attempts at Sending an Authentication Code | The maximum number of times that Intelligent Automation generates and delivers a new code. |
| Behaviour After Exceeding Maximum Code Send Attempts | When the Maximum Attempts at Sending an Authentication Code value is exceeded, Intelligent Automation behaves according to the value entered in this field. For example, if you enter agent here, Intelligent Automation will transfer the user to an agent. (what are the options here?) |
| Maximum Attempts at Verifying an Authentication Code | The maximum number of times that Intelligent Automation will process a verification request for a single authentication code. |
| Behaviour After Exceeding Maximum Code Verification Attempts | When the Maximum Attempts at Verifying an Authentication Code value is exceeded, Intelligent Automation behaves according to the value entered in this field. For example, if you enter agent here, Intelligent Automation will transfer the user to an agent. (what are the options here?) |
| Skip Options | If a user has passed authentication and the application returns to the module at any point, the application will not attempt to go through the verification process again. |
| Code Generation Options | |
| Select an option for the code generation | Options are Internal and External. |
| External Code Generation Options | |
| Prompt Wording | Enter a prompt. For example "Enter the verification code on your device to sign in." |
| Check Verified Contact Methods Web Service URL For Test Calls | ?? |
| Check Verified Contact Methods Web Service URL For Production Calls | ?? |
| Web Service Timeout (milliseconds) | When this value is reached, the code is no longer valid. When setting this value, consider the time it takes for the user to retrieve the code and the time it takes to enter it. |
| Internal Code Generation Options | |
| Number of digits for the Generated Code | Darren - I notice the screenshot displays 123. Is that the syntax used if you want to generate a 3-digit code? Or do you display a 3? |
| Internal Code Expiration Time (minutes) | When this value is reached, the code is no longer valid. When setting this value, consider the time it takes for the user to receive the code and the time it takes to enter it. |
|
Sender information that appears in the email or text message to the use |
At login
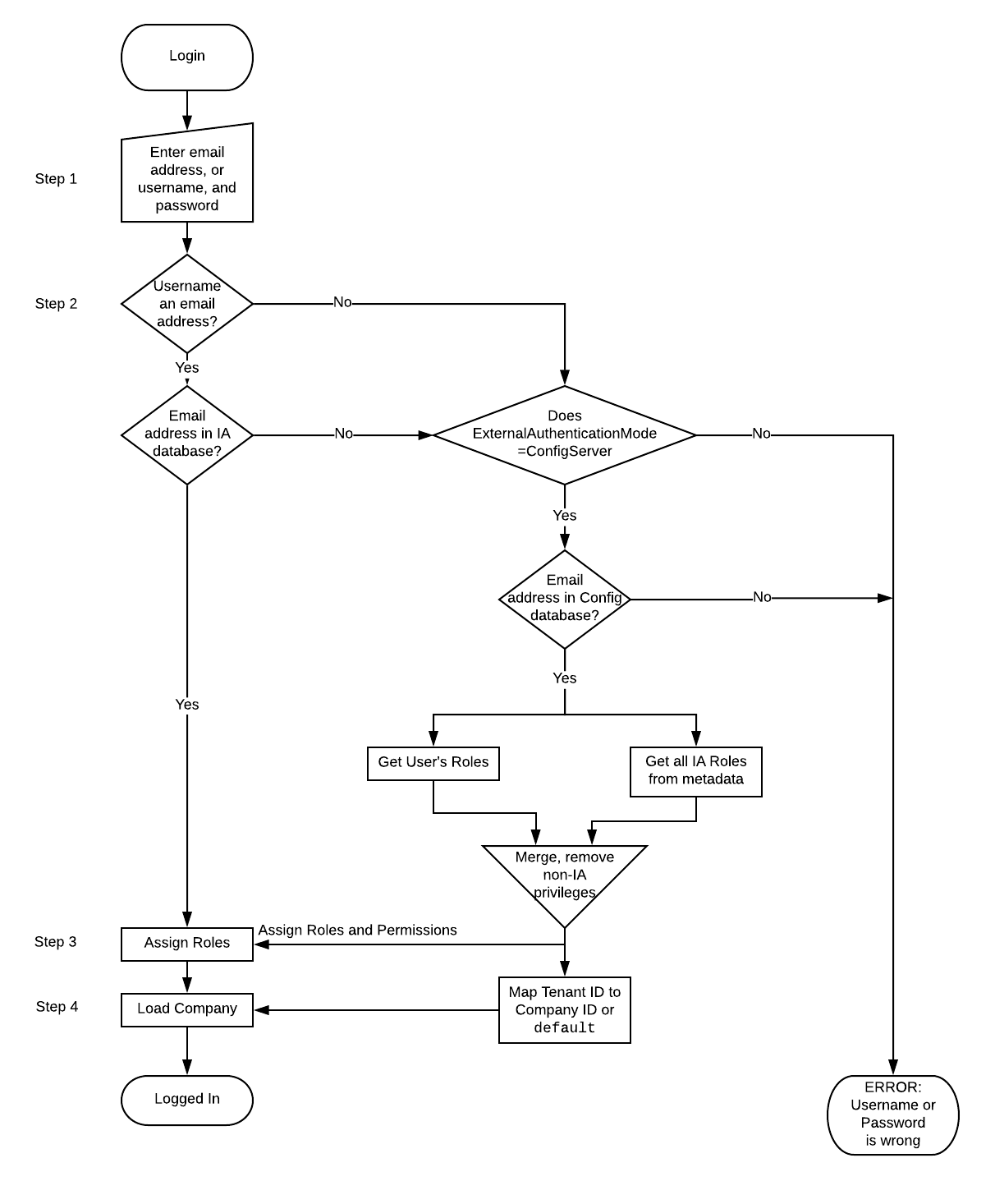
At login, the following high-level actions occur:
- The user enters their username and password. For internal users, the username is their email address. For external users, the username is their Configuration Server username.
- If two-factor authentication is enabled, the user enters the verification code generated by Intelligent Automation or by an external authentication application, depending on the user's preferences and settings.
- The user is authenticated, or validated, as follows:
- Without two-factor authentication enabled - Intelligent Automation compares the user's credentials to internally stored credentials in the application's database.
- With two-factor authentication enabled - According to the methods outlined above for internal authentication and for external authentication.
- Permissions and roles are assigned to the user, based on the information in their respective database. Permissions define what the user can see, while roles define what the user can do to those items it can see.
- The company associated with the user is loaded. For external users, the company is based on the Tenant ID with which the user is associated, or if no association is found, of the default company, set in of the parameter
With these four steps completed, the user is now in the Dashboard of the Intelligent Automation interface, ready to start working.
The following flow chart illustrates the login process:
Changing passwords for external users
Passwords for external users can be changed in Intelligent Automation. The process of managing them is completely transparent to the Intelligent Automation user.
If Change password at next login is checked in the external user's profile in Configuration Server when the external user logs in to Intelligent Automation, the user is prompted to change their password in the same way as for an internal user. See How do I change my password. The password is changed in Configuration Server automatically and Change password at next login is cleared in the external user's profile.