User Security
Writer's note: Opening sentence is revised to resolve jira ticket WFM-22283.
The Workforce Management (WFM) user security modules Configuration > Roles and Configuration > Users in WFM Web for Supervisors, enable you to fine-tune the precise access each user has to WFM modules, objects, and functions. For example, you can:
- Limit certain users so that they can view only certain sites or teams.
- Limit certain users so that they can read the schedule but not change it.
- Limit access to reports.
- Limit access to WFM configuration settings modules, such as Contracts and Time Off Rules.
Pending Schedule Changes
User security enables you to control who can make changes to schedule scenarios and to the Master Schedule. Users might be able to enter changes to the Master Schedule, but unable to commit or approve changes. Such changes are in pending status. An authorized user can then review the changes, and either commit/approve them or roll back/delete the changes.
This enables contact center managers to provide Master Schedule access to certain users who might not ordinarily have access. For example, supervisors who manage teams of agents, but who don’t normally have any scheduling responsibility, can enter team meetings or other exceptions into the schedule. Workforce-scheduling professionals can then review these to ensure that coverage is not adversely affected.
Genesys Configuration Manager
You define Switch, Person (agents and supervisors), Skills, and Time Zone objects in Management Framework Configuration Manager, which are then saved in the Configuration Database.
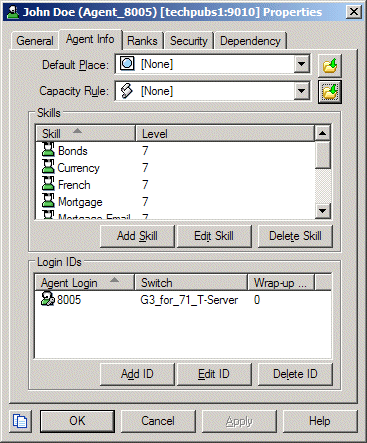
The figure below shows an example properties dialog box that opens when you click a Person (agent) object in Configuration Manager.
In the example above, note the Skill set associated with the agent.
Is Agent Field in Configuration Manager
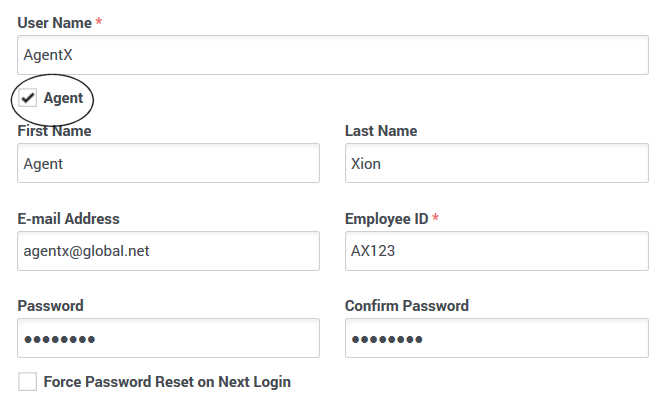
When importing users into WFM, users (non-agents) available for selection have the Is Agent check box cleared in the Configuration Manager Properties dialog box, as shown in the example below.
Configuration Manager Security
The Genesys security setup in Configuration Manager also applies to WFM. For example, a user who is logged in to Web for Supervisors, but does not have permission to view certain objects/users in the Genesys Configuration Layer, will not be able to view those objects/users in Web for Supervisors.
A user's ability to see, interact with, and synchronize agents and skills in WFM matches that user's tenant-based access permissions in the Genesys Configuration Layer.
In other words, in order to access an agent or a skill in WFM, you must be able to do it in Configuration Manager. The agent can be assigned or unassigned.
This access permission is tenant-based. If you are working in a multi-tenant environment, this behavior affects every display of agents or skills in WFM. Tenants exist only in a multi-tenant environment. For details about tenants, see the Framework Configuration Manager Help topic Configuration Database Objects > Resources / Tenants > Tenant Object Overview.
About the WFM Database
You create or update the WFM Database schema using the WFM Database Utility. You configure the WFM Database using WFM Web for Supervisors. For more information about the WFM Database Utility, see .
You configure the WFM Database using WFM Web.
Migrating Security Settings
If you are migrating from WFM 7.x, users are imported with the same security settings as they had previously.
Note: If the security settings have been broken down into more specific functions, users who had access to the functionality in the prior version keep the same permissions. However, in some cases you might want to adjust the security settings to take advantage of the increased granularity.
For example, users who had permission to edit the Calendar now have permission to Add/Edit/Delete items and to Prefer/Grant/Decline items. You can change the security settings to allow one set of calendar modification settings but not the other.