Single Sign On
Single Sign-On (SSO) identity authentication enables your users to securely access multiple Genesys applications with a single credential.
After entering their username in the application login screen, users will be taken to your company's authentication provider where they will enter their username and password. After that, they will not have to log in again until your authentication expires which is typically every eight hours.
You can enable Single Sign On for your environments in the SAML section under Single Sign On. Security Assertion Markup Language (SAML) is an open standard for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider.
Supported IDPs
Prerequisites
a. IDP metadata file – what is it, how does customer get it from their IDP? is there a difference between test and production idp? b. Username consideration – matching user name between IDP and Genesys. If username does not match, what is the process before setting up SSO (this maybe something to do to set up the test users) c. Describe the user who can access this – specific to Agent Setup Admin (role only) d. Access Group to be turn on – Test Access Group with username matching between Genesys and IDP e. Notice: SSO does not support users with multiple username, example User1_agent and User1_supervisor
Roll Out Strategy
a. Turning on Test IDP for Genesys test group i. Step 1 through N b. Turning on Prod IDP for Genesys test group, includes process to replay idp server with new one – going from test id to prod idp) i. Step 1 through N c. Rollout of SSO to each production group (include info like – downtime, user notification, user experience after sso are turn on) i. Step 1 through N
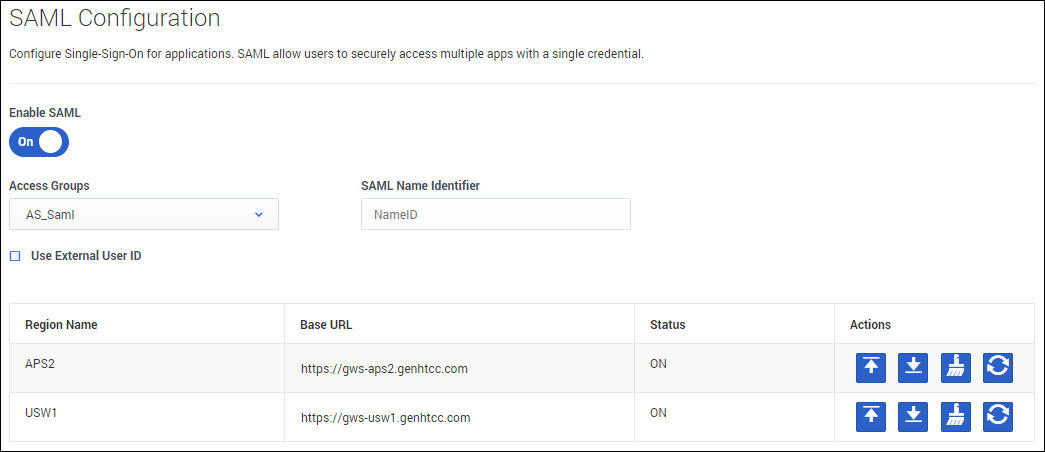
To enable SSO for your environment, first turn on the Enable SAML toggle and begin identifying the Access Groups and Regions you want to enable. Select one or more Access Groups from the groups in your tenant environment and provide the NameID of your IDP file of your SAML assertion in the SAML Name Identifier field.
If you are using an external identification provider, select Use External User ID.
The regions in which your contact centers are located are listed in the table. For each region, this table includes your Base URL, which you can edit; the SAML status (ON, OFF, PENDING); and the Actions you can take with each region.
The Actions include:
- Upload IDP-Metadata allows you to upload your metadata.
- Download SP-Metadata allows you to download SP metadata for your use. This is available after your IDP metadata has been uploaded.
- Clear IDP-Metadata allows you to clear previously uploaded metadata in order to upload new metadata.
- Reload SAML setting forces a refresh of the metadata automatically, avoiding an approximate five-minute wait time.
Rollback
– What is the step to rollback SSO for a certain group or all