Setting up mailboxes for OAuth2
Follow all the steps in https://docs.microsoft.com/en-us/azure/active-directory/develop/scenario-daemon-app-registration to create an Azure application for the mailbox(es) that will be accessed by Genesys Email Server.
In step 6,
Select Accounts in any organizational directory (Any Azure AD directory – Multitenant) Leave the Redirect URI empty
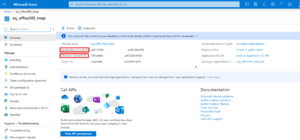
After the application is created, it should look like:
Where, esj_office365_imap is the Azure application name. Please record the Application (client) ID and the Directory (tenant) ID, they should be provided for configuration.
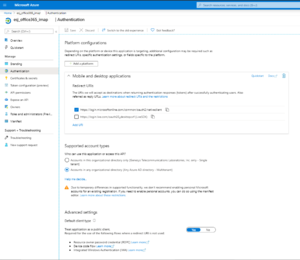
If you open the Supported account types and Redirect URIs, it should look like:
The Application ID URI should be empty:
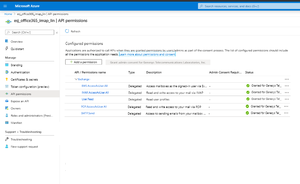
Add Application Permissions
Read https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent to understand permissions and consent.
This is a good reference document https://docs.microsoft.com/en-us/graph/auth-v2-service#2-configure-permissions-for-microsoft-graph, although it focuses on getting permission for the Graph API. For IMAP and EWS, the application should have the following permissions granted by the Company Admin depending on the email protocols used:
(To confirm if SMTP is needed and pop3 )
Mailbox Setup
The mailbox has the following special settings in the company’s system:
Mult-factor authentication is disabled on the mailbox
IMAP protocol is enabled (if IMAP is used)
POP3 protocol is enabled (if POP3 is used)
No need for EWS protocol.