Contents
User Authentication and Authorization
New section
This section describes how Genesys Intelligent Automation ensures that only authenticated and authorized users access Intelligent Automation environment specifically, and the Genesys software environment generally.
For more information about user authentication and authorization, refer to the User Authentication and User Authorization section of the Genesys Security Deployment Guide.
Users
There are two types of users in Intelligent Automation:
- Internal users: Created, managed, and stored internally in Intelligent Automation. See the Users page in Intelligent Automation Help]]. These users are not subject to an external authentication engine; all authentication is done by Intelligent Automation. All authorization is implemented through Roles.
- External users: Created and managed in Genesys Configuration Server, and stored in Genesys Configuration Database. All authentication and authorization is done in Configuration Server. External users are supported starting in release 9.0.004.00.
The two user types mean that when creating a new user, the administrator must first decide whether to create the user in Intelligent Automation or in Genesys Administrator.
Prerequisites for external users
If you are working with external users, you must do the following:
- Enable Intelligent Automation to work with external users.
- Configure Intelligent Automation access to Configuration Server.
Configure working with external users
To configure Intelligent Automation to work with external users, set ExternalAuthenticationMode in the Default Server Settings tab under Administration in the Intelligent Automation interface, as follows:
<insert screencap or setting>
Configure access to Configuration Server
To configure Intelligent Automation to work with external users, Intelligent Automation must call upon Configuration Server to, among other things, validate the user. Therefore, you must provide the information required to access Configuration Server in the Default Server Settings tab, as follows:
<insert list or screencap of settings>
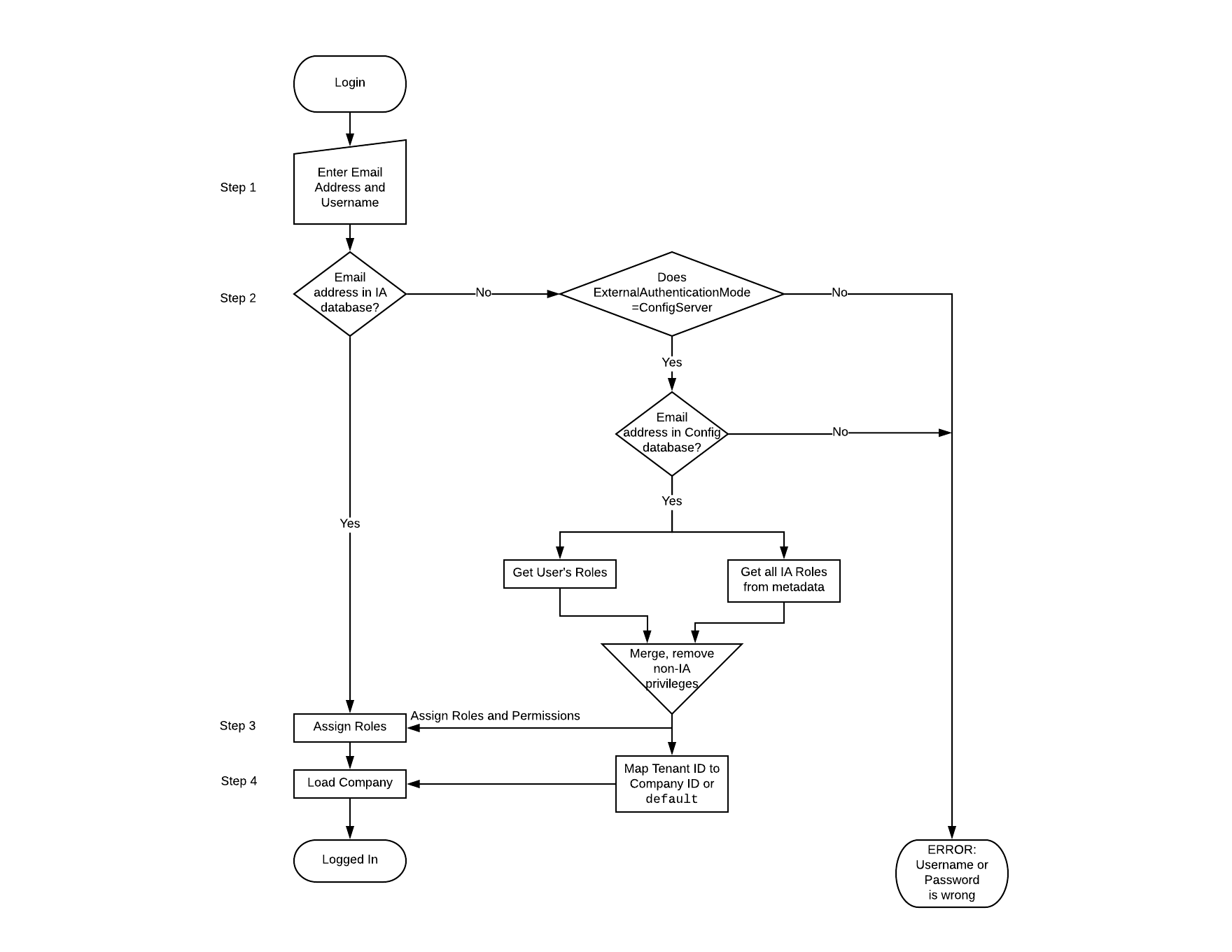
At login
At login, the following high-level actions occur:
- The user enters their credentials, in this case their email address and their password.
- The user is authenticated, or validated, by having their credentials compared to internally stored credentials in the application's database.
- Permissions and roles are assigned to the user, based on the information in their respective database. Permissions define what the user can see, while roles define what the user can do to those items it can see.
- The company associated with the user is loaded.
With these four steps completed, the user is now in the Dashboard of the Intelligent Automation interface, ready to start working.
The following flow chart illustrates the login activity: