Contents
Role-Based Access Control
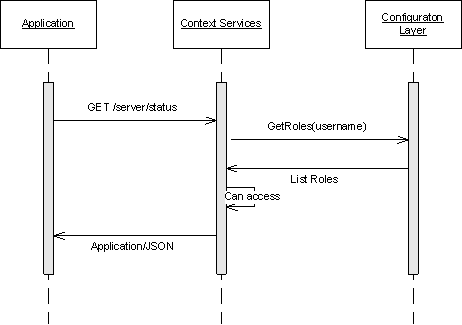
This page describes how you can implement the role-based access in the Context Services.
Configuration
Through Configuration Manager or Genesys Administrator, you can define roles for your application built on top of the Context Services. To do this, you assign one or more roles to your users when creating your application's configuration in the Context Services. You are responsible for creating and defining these roles, where each role is a collection of Genesys Administrator Tasks associated with permissions.
<tabber> GMS/CS=
Rights for GMS/CS
|
Tasks related to Service management are available in GMS and may require specific permission set up in Genesys Administrator. |
In 8.5.0, privileges are simplified for GMS/CS.
| Name | Description |
| Administrator | Specifies write access to all CS APIs. |
| Supervisor | Specifies read access to all CS APIs. |
The following table details the relationship between requests and privileges.
| HTTP Operation | Required Permissions |
|---|---|
| PUT | Administrator |
| POST | Administrator |
| GET | Administrator or Supervisor |
| DELETE | Administrator |
Click here to learn how to create roles and assign privileges.
|-| UCS/CS=
Genesys Administrator Tasks for UCS/CS
|
Tasks related to Customer management are available in UCS and require specific permission set up in Genesys Administrator. |
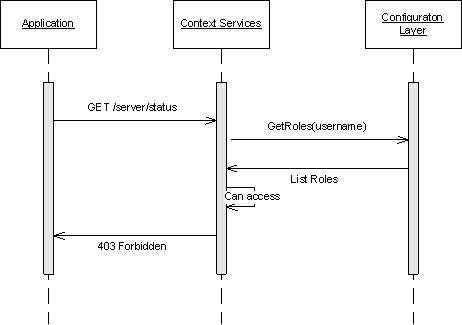
Once authenticated, if the use-role option is set to true in the configuration (see the options defined in authentication Section) then the Universal Contact Server checks that each operation is allowed. If not, Error 403 forbidden is returned.
Mapping Genesys Administrator Task with Context Services
Operations can require that one or more Genesys Administrator Tasks are allowed, according to the type of data that the request modifies. If your application's role does not allow all of the rights required for a given operation, then the operation does not proceed.
For example, consider that your application performs a Create Customer Profile operation with extensions. If your application's role allows UCS.Customer.createProfile but not UCS.Customer.createProfileExtension then the profile is not created. Your application instead receives a HTTP 403 Forbidden error.
| Operation | Genesys Administrator Tasks | |
|---|---|---|
| Profile Operations | ||
| Create Customer Profile POST /profiles
|
| |
| Delete Customer Profile DELETE /profiles/${customer_id}
|
| |
| Delete Record From Profile Extension PUT /profiles/${customer_id}/extensions/${ext_name}/by/unique
|
| |
| Identify Customer GET /profiles
|
| |
| Insert Extension Records POST /profiles/${customer_id}/extensions
|
| |
| Bulk Profile Import POST /profiles/import
|
| |
| Query Customer Profile GET /profiles/${customer_id}
|
| |
| Update Customer Profile PUT /profiles/${customer_id}
|
| |
| Merge Customer Profile PUT /profiles/${customer_id}/merge/${src_id}/
|
| |
| Update Record In Profile Extension PUT /profiles/${customer_id}/extensions/${ext_name}/by/unique
|
| |
| Schema Operations | ||
| Create Profile Extension Schema POST /metadata/profiles/extensions
|
| |
| Create Identification Key POST /metadata/identification-keys
|
| |
| Get Identification Keys GET /metadata/identification-keys
|
| |
| Query Profile Schema GET /metadata/profiles/
|
| |
| Query Profile Extension Schema GET /metadata/profiles/extensions
|
UCS.SchemaMgt.readProfileExtensionSchema | |
| Query Business Attribute Schema GET /metadata/business-attributes/${business-attribute-name}
|
| |
| Get Metadata Cache GET /metadata/cache
|
| |
| Change Metadata Cache PUT /metadata/cache
|
| |
| Get Metadata GET ${contenttype}} /metadata
|
| |
| Delete Metadata Profile Extensions DELETE /metadata/profiles/extensions/${extension-name}
|
| |
| Delete Metadata Identification Keys DELETE /metadata/identification-keys/${id_key-name}
|
| |
| Interaction Operations | ||
| Query Interactions GET /customers/${customer_id}/interactions GET /services/${service_id}/interactions GET /interactions/${interaction_id}
|
| |