Role-Based Access Control for FA
When managers log in to the Frontline Advisor dashboard or the administration module, they are presented with a customized view of agent groups and agents relevant to them. With the introduction of role-based access control (RBAC) to Frontline Advisor, it is no longer assumed that managers can navigate to all child nodes simply because they have access to the parent. The opposite is also true; if a manager has access to child nodes, that manager does not automatically have access to the parent node. You can configure permissions in Configuration Server such that a user can view only specific levels of the hierarchy.
For example, a group leader sees all teams and agents under them, but might see only the aggregated values at higher-level nodes in the hierarchy. To perform threshold or rule overrides at a given node, the manager must have explicit Change permission for that node granted by an administrator. In this example, the group leader is granted Change access at the group level and below, but not at higher level nodes (because changes would affect other groups not even visible to this group leader).
Interaction on the Thresholds tab of the FA administration page is controlled by a user’s access to metrics. A user can view and override only thresholds where they have access to the corresponding metric. Access to the metrics and levels in the hierarchy determines which metrics and levels the user sees in the administration module.
Example of RBAC Use
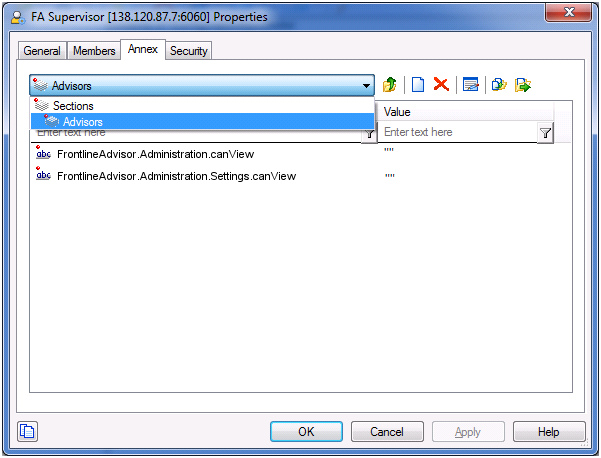
RBAC can control access to areas of the FA administration page. For example, the Settings tab on the FA administration page is displayed only if the user has explicit role-based access to it. If such access is granted, it is granted to all settings, not just the ones that relate to the manager’s team of agents. Access to the Hierarchy Reload section of the Settings tab is controlled separately. A user might have access to the Settings tab, but not to the Hierarchy Reload portion of the tab.
In this example, our user is called FA Supervisor. To configure the scenario described above for this user (allow access to the Settings tab, but restrict access to the Hierarchy Reload section), you assign privileges to the FA Supervisor role using Configuration Manager.
See FA Access Privileges for the list of Frontline Advisor privileges, including notes about privilege dependencies.